Effortlessly Safeguard Sensitive Data.
Everywhere.
Dynamic Next-Gen Data Security Platform
Don’t Leave Your Cybersecurity Stack Incomplete, Lock Down the Crown Jewels, and Reduce the Data & Compliance Risk Impact by Over 90%.

The weakest link to your sensitive data is likely the lack of visibility. Adding more traditional Cybersecurity locks and fences at the perimeter, such as Firewalls, Endpoint Detection and Response (EDR), and DLP is not enough. By leveraging Actifile’s game-changing Data Security Platform, you can quickly identify and protect your sensitive files across the organization where your traditional Cybersecurity stack falls short.
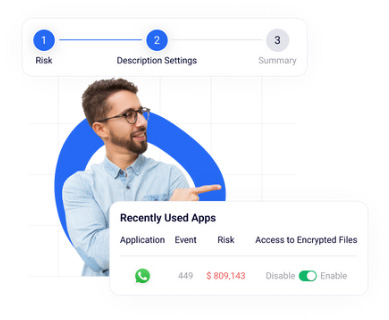
Monitor Sensitive Data on One Centralized Platform
- Ensure compliance with data and privacy standards and regulations
- Minimize data breach risks, whether from ransomware or insider threats.
- Offer crucial forensic evidence post a breach.
The Next-Gen Approach to Data Security
- Discover and Classify Sensitive Data
The Actifile AI Autonomous Sentry continuously scans the environment to identify all data files. - Quantify the Risk
Automatically assigns monetary risk values to all data - Monitor the Flow of Data
Continuously tracks and reports on all sensitive data (movement, access, changes, etc.) - Dynamically Encrypt All Identified Data
Automatically protects (encrypts or blocks) Sensitive Data based on dynamic scalable rules – reducing monetary risk by +90%

A Quantum Leap in Data Security
- Reduces monetary risk by +90% within hours (10% risk reduction has been the gold standard for legacy solutions
- Is simple to deploy and manage
- Utilizes transparent encryption, eliminating the impact on employee productivity
- Compliance standards can be achieved within hours instead of months
How it Works
Actifile connects to your sanctioned applications like Office 365 and Google Workspace to gain visibility into content created and shared natively in the cloud.
There are 3 remote deployment options:
- For workstations and laptops: Windows, MacOS and LinuxVM
- For server OS: Windows and Linux
- For cloud-managed file repositories like Office365, and Google Workspace (Amazon S3 and others are coming soon), through standard Cloud API connectors.

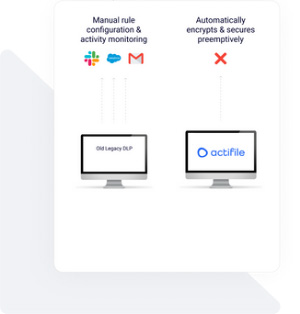
Simplify data security by switching from “chatty” DLP methods, that require handling of each and every event, to preemptively encrypting each sensitive file in advance. Instead of blocking each option to exfiltrate sensitive files through any type of application, applying automatic encryption secures the file, and in the event of the file being stolen or leaked – it will not open without Actifile Sentry and the organization’s decryption key. However, sensitive files are peppered throughout the organization, with multiple file types and file locations, and new ones are always being created. The approach has to be top-down and efficient, and this is where data risk monitoring and quantification helps greatly.
Smooth, Secure, and Flexible Encryption with the Actifile Encryption Wizard
The Actifile Encryption Wizard is a proprietary interface to get the job done with just a few clicks. By leveraging the OS AES 256 standard encryption libraries, all existing and future files with the sensitive data tag are automatically encrypted. Files are decrypted from wherever they reside: on the endpoint, or a file server, or on a cloud app. There’s no need to enter usernames or passwords. The encryption is instant with zero latency.
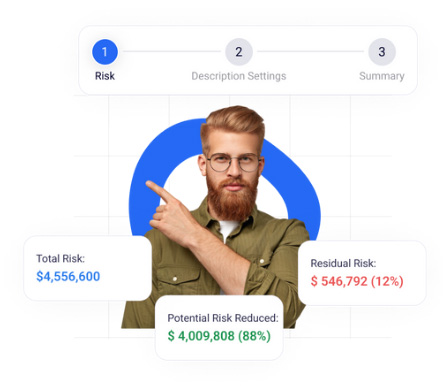
A Unique Top-Down Approach
Secure the risk types you want to automatically encrypt with this user-friendly and intuitive wizard. For example, if Actifile identified USD 2.6M for Credit Card PII across 26 file instances , 12 file types and 7 locations, the Actifile Encryption Wizard will show you how to encrypt all of them with one click.